The Netherlands was plagued by numerous DDOS attacks lately. The tax authorities, Bunq bank and many other banks and government agencies. The attacker was careless and left some traces and was even arrogant enough to seek contact with the sysadmin of Tweakers.net, one of the targeted sites.
Background
Tweakers.net published a very nice article (original in dutch) describing the complete timeline of the attack and investigation from their perspective.
The attacker, Jelle S., an 18 year old male from Oosterhout, had been caught by the Bunq bank before. In September 2017, Jelle executed several DDOS attacks on the Bunq bank. After extensive research, Bunq discovered that Jelle was behind the attacks. They did not press charges, because Jelle showed remorse. How wrong could they be…
The second wave of attacks on Bunq started in November 2017. Bunq immediately reported it to the police and the police started an extensive investigation. The third wave of attacks started at the end of January 2018 and targeted many more sites. Eventually Jelle was arrested the first of Februari.
The attacker
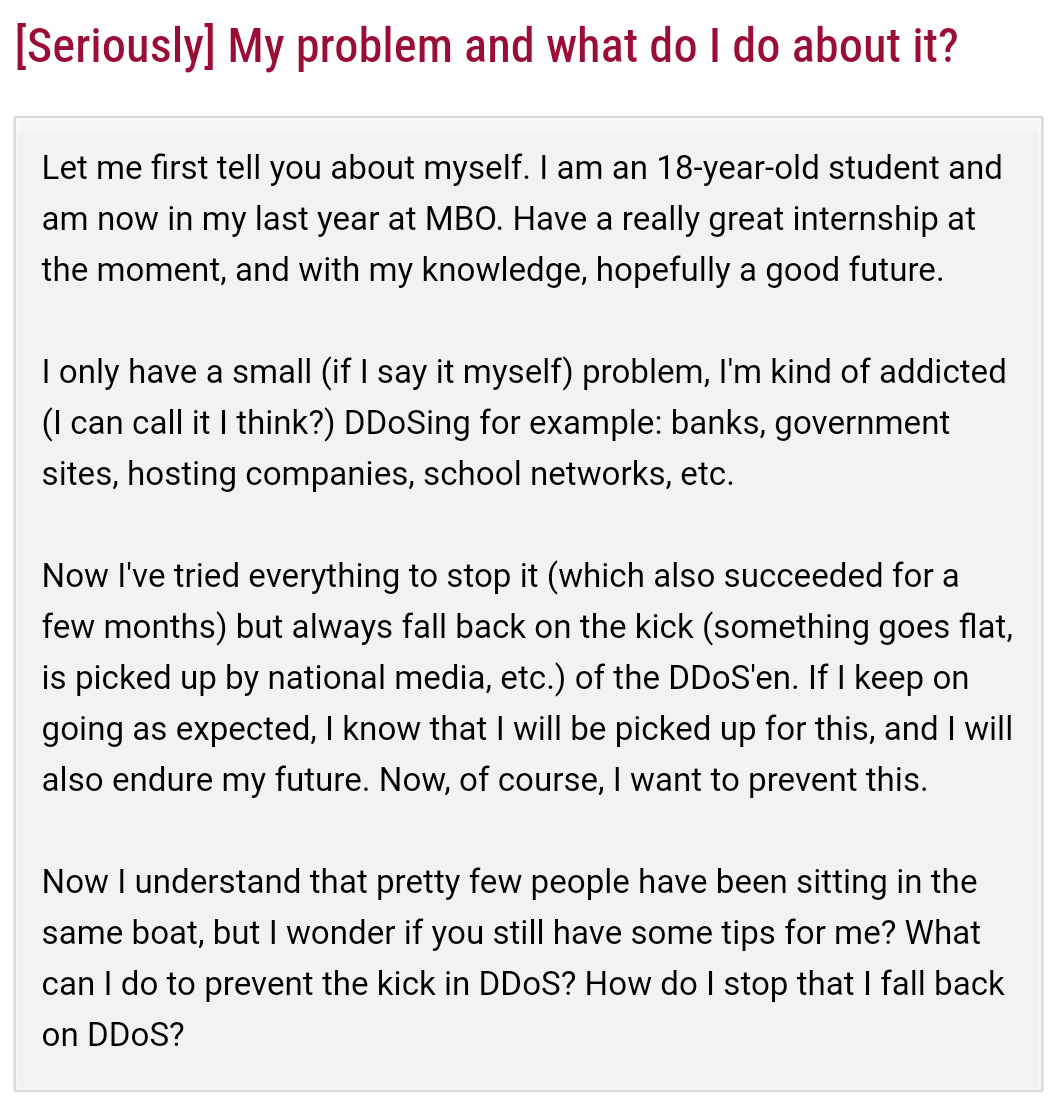 Coincidentally, at the end of December, I stumbled upon a
forum post
on Tweakers.net (original in dutch).
An 18 year old male was seeking help for his small problem (how he
described it himself) of being addicted to DDOS attacks on banks,
government agencies, school networks and hosting providers. I guess
Jelle just does not see the seriousness if his actions. It seems
like a game to him. The forum thread was soon closed, simply because
Tweakers.net has strict rules and does not allow discussion about
criminal activities.
Coincidentally, at the end of December, I stumbled upon a
forum post
on Tweakers.net (original in dutch).
An 18 year old male was seeking help for his small problem (how he
described it himself) of being addicted to DDOS attacks on banks,
government agencies, school networks and hosting providers. I guess
Jelle just does not see the seriousness if his actions. It seems
like a game to him. The forum thread was soon closed, simply because
Tweakers.net has strict rules and does not allow discussion about
criminal activities.
DDOS - DNS amplification attack
Executing a DDOS is not very complicated. In this case Jelle had bought 40 euro of capacity at a stresser. A service to test your own infrastructure for its DOS handling capabilities. Ofcourse you can also target other sites with it.
The technique used was a DNS amplification attack. Simply said, having very many clients (e.g. a botnet) send as many DNS requests possible to many DNS servers. The request has spoofed the source address to be the victims address and it queries all known information of a DNS zone in one simple and small request. This results in an extreme amount of data being sent at the same time to the victims address.
Wrap up
The attacker reminds me of the behavior of some arsonists. They mingle in the crowd, watching the fire do its job.
He is simply not aware of the severity of his actions. Seeking recogition for his actions, submitting news items, contacting the sysadmin, hanging around to see his results. This all got him caugth. Worst of all, he did not learn from his first offence, where he was very lucky not to be prosecuted. The only fortunate thing is that he is aware of his addiction…